Key Simple Security Steps - 10 Tips on How to Not Get Hacked
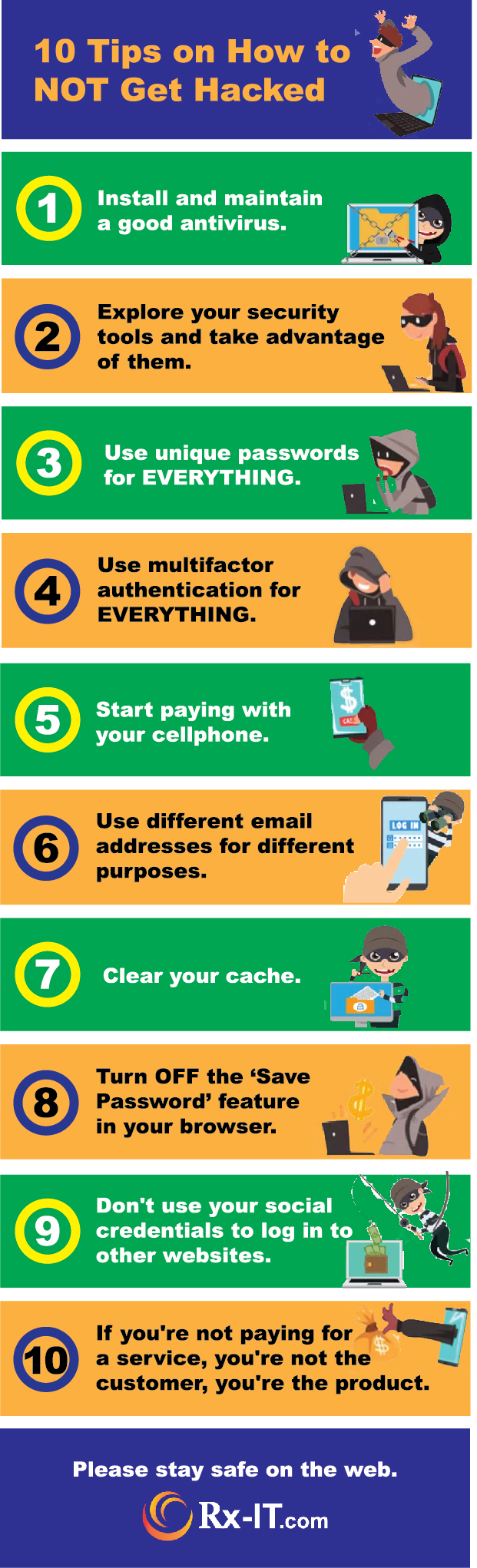
10 steps that will help keep you safe and hack free when combined together.
There's no one thing that you're going to do, that's going to keep the bad guys out.
There's a number of things that you do together. And this webinar is really about you personally, as opposed to just a business environment.
This is you at home. This is you at work. This is just all around stuff to do with technology and with your day to day life in technology.
1. Install and Maintain a Good Antivirus

The first and most important thing is to install and maintain a good antivirus. We call this type of software antivirus but fending off actual computer viruses is just a small part of what they do. Ransomware as you know, it encrypts your files, and it demands payment to restore them, and Trojan horse programs. They look like valid applications. But behind the scenes, they steal your information. And then there are bots that turn your computer into a soldier in a zombie army ready to engage in denial of service attacks or spew spam or whatever the bot herder commands.
The bot herder is the person who's controlling the bot from Russia or, or somewhere in Southeast Asia. An effective antivirus protects against these and a lot of other kinds of malware. I put Avast up there because it's free, but the other guys are better.
Bitdefender is fantastic. Webroot's really good. Kaspersky used to be on my list, it used to be if you bought a computer at Costco, you would get a year or two of Kaspersky for free. Kaspersky is a Russian company, we've had to cross it off the list, we know that they're, you know, some shenanigans going on with that. There are other anti viruses as well, I don't, I don't recommend anything else.
If you're in your business environment, and it's a business computer, what we really recommend is something that's more of an enterprise grade like Sentinel One- which is what we use for our clients, that is SOC monitored. A SOC is a Security Operation Center. What that means is there's somebody manning that, seeing the data, the antivirus data from your computer, in real time, and ready to act on that. If something got through, we would be alerted immediately and we'd be able to get in there and shut that down.
If you need more information about that, my contact information is at the end, feel free to reach out to me but I'd suggest you reach out to your IT people and just say hey, we got this kind of thing. We need this kind of thing. And the term is SOC. I'm sure they'll know what that is.
In theory, you can set and forget your antivirus protection, just let it go along in the background. It'll download updates. In practice, you should look at it every once in a while. Most of the utilities and antivirus display a green banner when everything is okay. If you open the utility and you see yellow or red, just follow the instructions and get things back on track. Again, if you need that, if you're a business, you really need a SOC monitored security application. Talk to your IT people.
Isn't Antivirus for Windows free and built in?
The answer is yes. Not only is it baked into the operating system, it automatically takes over protection when it detects that there's no other antivirus installed. And it automatically steps aside if you install one of those third party protections.
The built-in antivirus really doesn't compare to these other guys. Except there was one time that I remember in recent history where there was a piece of ransomware that was out there in the wild. What 'in the wild' means is that the antivirus softwares don't know about it yet. So it's in the wild until they get it into their definitions.
Most of the antivirus software, including Windows Defender, have some in the wild detection capability. Nobody detected this ransomware except Windows Defender. So I do recall that and say that it does have its moments. But I wouldn't rely on it, I think you can do better. So if you can look at one of those other ones.
2. Explore Your Security Tools

The next thing that we want to recommend is that you explore your security tools, there are things like 'find my phone', all you have to do is turn it on, well, it's not enough to just turn it on, test it, make sure it works, make sure you can actually find your phone.
A lot of the anti viruses that we talked about, they have something built in called PUA Protection. By default, a lot of the time it's turned off, because PUA's are potentially unwanted applications. They're not viruses, they're not necessarily malware, but they don't do anything useful. They do things like take your information to sell it to other people or to other companies and whatnot. Sometimes they've been known to actually let others use their position of trust on your computer, if you will, to let other applications be downloaded and installed. You want to go through and make sure that that kind of thing is turned on. I'd really recommend that you turn on during some downtime, flip through all the settings in the tabs and just see what's in there and what it can do and make sure that it's all turned on that it's that it's all good.
Andrew. Did you have any feedback on this?
Yes, flip through all the settings, tabs. My process is to click all the things and turn it on until your computer doesn't work well. Then unclick some things until it works good again, and then you'll know.
We remember the days when there was any antivirus on your computer, you could always tell when it was doing a scan, because it would grind everything to a halt. Fortunately, it works a lot better these days.
This is a really good website to go to. There's an organization called Amped, the anti malware testing standards organization. And if you go there on your computer, or even on your phone, Android or iPhone. https://www.amtso.org/security-features-check/
You can go to this website and there's a few different little tests you can do. Basically, it'll test your computer and make sure that you've got adequate protection. So do that. Why not? It's free. And if your antivirus doesn't pass, it's time to contact tech support and find out why.
3. Use Unique Passwords for Everything

The next thing that we want to say is you need to use unique passwords for everything. Everything.
One of the easiest ways that hackers steal information is by getting a batch of usernames and passwords from the dark web or someplace. They try those same combinations elsewhere, they try them on your Facebook page, and anything else they can think of, you know, bank sites and whatnot.
Let's say the hacker gets your username and password by hacking an email provider, they might try to log into banking sites, major online stores using the same username and password, the single best way to prevent a data breach from having a domino effect is to use a strong unique password on every single account that you have. The way to do that these days is using a password manager. We did a webinar on that last month. So if you need more information about that, please, ping me and I'll be happy to help. It's a really, really almost mandatory thing for you to do nowadays.
4. Use Multifactor Authentication for Everything

Use multifactor authentication for everything for Gmail, for Evernote, for Dropbox for Amazon. If you just use a password for Authentication, anyone who learns that password owns your account, and with multi factor authentication enabled, the password alone is useless. And most password managers now support multi factor. Some only require it when they detect a connection from a new device. Enabling it for your password manager is an absolute must, because that's the key to the kingdom.
I want to cover the four types of the four main types of multifactor authentication.
The best, the one that we like the best is using an authenticator app. They're free, you can download one from Authy, from Google, from Amazon from Microsoft. If you're a business customer with us, we prefer one called Duo. It's a little more secure, we can manage it for you. And help you out with that. Sometimes you have an option to get a phone call. You know, it's not as good as an authenticator app, but it's still good, right? They're gonna call you on the phone and you're gonna press one for Yes, let the guy allow it or two for No, don't allow text message. We're all familiar with that. That's really probably the most common form of multifactor today.
Know that your phone number can be hijacked. There are ways for me to learn some information about your phone, and then have that number all of a sudden ring to my phone instead of your phone. So I can intercept your text messages.
The last way is the way we decide these security questions.
What's your favorite color? What's your favorite food? What's the name of your girlfriend or your first girlfriend or your first boyfriend? These are terrible. I mean, this is information that people can find out about you. You just don't know what's out there about you on the internet, or what people can easily learn from you. Somebody calls your house and your kid answers the phone and they say, 'Hey, What's mommy or Daddy's favorite color', and kids want to be helpful. And that's kind of a wild example. There's just lots of if you put your mind to it, there's lots of different ways to learn information about people.
Andrew, do you want to say anything about multi factor authentication?
Sure. So security questions are a substitute for multi factor authentication, right? It's, you know, it's not very good. If you have some high security things, too, it's getting easier. It's kind of a pain. But you know, physical tokens, like a little USB thing, or a thing you tap on your phone are getting more popular, you probably would only use those with bank accounts or stuff that, you know, you need to keep really secure. But, those are an option where you have something you really don't want other people to get at.
I've been using Google. It has a program where you can enable high security and you use like tokens with it's really for journalists that are, you know, trying to be secret, but I've been using it for a couple of years. It's not bad. But you have to have a physical key. So, it's really hard to get into my Gmail, but on the other hand, I have to have those physical keys. What would happen if you lost that key?
They have a whole system. So you have to have two keys you have to like. They have ways to get in But it involves a waiting period if I lost those keys,
Use passcodes, even when they are optional.
If you have a device managed by us, a business device, a business phone or whatnot, and it's managed by us and you're using your 365 on there, we're going to make you have a passcode on there, right? But it's necessary. Put a password on your smartphone, put a password on your iPad. And, you know, it doesn't have to be a passcode, it could be facial recognition, could be a fingerprint, but have something on there because, those things get lost, they get stolen.
5. Start Paying with Your Smartphone

Here's a new one, at least new for me. Start paying with your smartphone. The system of credit card use, it's outdated, it's not very secure at all. Setting up your smartphone as a payment device is a very simple process. It starts with snapping a picture of the credit card you'll use. It pretty much ends there and you're ready. Some of the more popular I've listed some of the more popular payment applications, if you're on an iPhone, obviously Apple Pay if you're on Android, the most common Android now Samsung, so I have Samsung Pay, it's when I use Paypal has an app, Google has an app, of course G pay, Zell is becoming really popular. That goes directly to your bank account in and out of your bank account. If you're with Bank of America, if you're with Wells Fargo, if you're with Truest I know those three. Also, I just learned this, it doesn't work with any foreign banks, because I just had somebody who was in Germany wanting to pay us with a payment app. And I asked him to use Zell and they couldn't do it.
6. Use Different Email Addresses for Different Purposes

This one I get I get some pushback on. And I'm going to tell you up front that I'm not really good about doing what I'm about to preach. I do it to a very small extent. And I'll be candid about how I do it, I could be more secure with it if I were more organized. People who are both highly organized and methodical about their security, will use different email addresses for different purposes. They want to keep the online associates of the online identities that are associated with different functions separate. Banking is a really good example, or personal business, if you have an email address that you just use for banking, and you never use it on social media, you know, the chances of somebody guessing that as the username for your bank account go way way down.
If a phishing email claims, you know, comes to you and it claims to be from your bank, and it's an account you only use with social media, then you know, it's fake. Now, let me be honest about how I do that there are people who have one for social media, one for you know, trying out apps or trying out free stuff, and they go and put that junk email address in and then they use one for the shopping, for Macy's and for the grocery store. And all those people who want you know, they want that information they sell, you're selling them that information, right? Because you're getting discounts at stores by giving them that information and then using it every time you go shopping using a little card or whatever your phone number, so that they can keep track of you.
Then having one that is separate for just your family, so no business related stuff it just family and friends. I'm going to tell you, I couldn't do that would drive me crazy. I have three. I have one for work. I have one that's personal for friends and family. The little bit of social media that I do is on that one, then I have a junk one. And that's the one I use for shopping and trying out apps. It's a Hotmail address. I've had it for years.
Do you want to say anything about this, Andrew?
You're probably familiar with this Bill. It depends on the system. But there's kind of a halfway you can do with this too, which doesn't give you a different email address, but lets you use different email addresses. So Gmail is one of the biggest ones that allows this. They allow what's called plus addressing. If you want to obscure your user name, it wouldn't necessarily stop somebody from figuring out what your email address is. But if you want to use different usernames, you may not know that my email address is gmail a sharife @gmail.com. I put in a sharees + spotify @gmail.com, that email will deliver to me. I'll be able to see that it was sent to the plus Spotify address. I could use that as a user name at Spotify. If I wanted to separate out my usernames, I know some people use it for them, they can figure out who's selling their information, because they'll know by which email address it comes to, that's not a bad intermediate step. You could always block email to a certain address when you stop using it via Gmail. So it's kind of a good in between step, it's not really another email address.
I had forgotten, you could do that with Google. So thank you for that. That's really good information. Maybe I'll give that a try. Because I need to separate out the stuff more.
7. Clear Your Cache

Our next security tip is to clear your cache. I can't emphasize that enough. Never underestimate how much your browser's cache knows about you. Saved cookies, saved searches, web history, points to your home address, family information, other personal data. Once in a while, really more often than I do it. Hit Ctrl + Shift + Delete. It'll bring up the dialog that lets you choose which elements of browser data that you want to clear. You don't have to clear everything, you can select which cookies you want to clear, it's very granular, you can choose just to clear from certain websites that have put cookies on there, and whatnot. That's an important thing. And again, it's very disconcerting, to go in there and start looking and finding out what your browser is retaining about you and about your online activity.
8. Turn Off the Save Password Feature in Your Browser

It's best to leave password protection to the experts who make password managers, we are positive that you know, you need to turn off the Save Password feature in your browser. Yes, it is super convenient. To save those passwords, it's super convenient to store the credit card information, the password managers will store your credit card information, and they'll do a better job of keeping it secure.
Think about this, when you install a third party Password Manager, it typically offers to import your password from the browser storage. And it doesn't just like that, if the password manager can do that, you can be sure that there's plenty of malicious software out there that can do the exact same thing. I've seen it work. I've seen how fast that malware on your computer that you know you might have inadvertently picked up from a website can download that information. It's scary. So if you miss anything today in this webinar, don't miss this. Turn off save passwords in your browsers, and keep your passwords in a single central Password Manager. It lets you use them across all browsers and all devices. If you've got the password manager on your computer, and on your phone, then you've got the same safe password information.
Andrew, do you want to add anything about how bad it is to save passwords in the browser?
Imagine the most hacked Password Manager in the world has to be the password manager in Chrome. The whole world fights to be your default, and you just install Chrome and it offers to save the password. And there you have it. Everybody's got some passwords saved in Chrome, if they haven't specifically eliminated it. So it's just the absolute most popular one. All the criminals are working on taking passwords from it.
You need to turn off the Save Password feature in all your browsers.
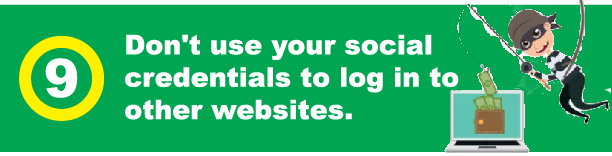
You can download your Facebook data and, and see just what the what the you know what they know about you. And I've included the link there, Andrew, if you could paste that in as well. But this is an article on PC mag about how to download your Facebook data. And you should do that. It's really eye opening, especially if you're the kind of person who routinely clicks on quizzes, that requires access to your social media account. And really, you don't need to know which Disney Princess Princess or dog breed you are. Just don't. And it's it's you know what they're doing is, it's freaky, it's scary. You can drastically reduce the amount of data going to Facebook by disabling the sharing platform entirely. Once you do, your friends can no longer leak your personal personal data, you can't lose data to apps, because you can't use apps. And you can't use your Facebook credentials to log in to other websites, which was always a bad idea.
I know it's convenient, but it's a really bad idea. Google probably knows more about you than Facebook. Take steps to manage your Google Privacy too. Here is a link there on how you can do that.
Make sure you configure each social media site so that your posts aren't public. Both Twitter and other broadcast media services. Think twice before revealing too much in a post since your friends might share it with other people. Other than that, you can retain your privacy without losing the entertainment and connections. It just takes a little work and a little bit of care.
10. If You're Not Paying for a Service, You're Not the Customer, You're the Product

This is protecting your social media privacy. Here's what I want you to take away from this, if you're not paying for a service, you're not a customer, you're a product. If you're not paying for a service, you're not the customer, you're the product.
Do you want to add anything to that Andrew?
I just posted the links in the chat.
https://www.pcmag.com/how-to/how-to-download-your-facebook-data-and-6-surprising-things-i-found
https://www.pcmag.com/how-to/how-to-manage-your-google-privacy-settings
It's probably in that article on Facebook, there's a ton of stuff you can change on Facebook. The defaults are pretty good. Even if they offer you options to kind of tighten up the defaults are always here's all my stuff, right?I don't know if anybody's keeping count or not. But that was the 10th Tip.
We're going to post this on YouTube later. And you could go back through and I really should have just listed all 10 on the first slide. I think I'll go back and do that. That is the conclusion.
There's nothing on here we're selling today. This is all absolutely free so you can expect to pay zero.
This is my contact information. If you have any questions or you want any follow up at all, if you click on this link, which Andrew will post in the chat.
That will take you to my calendar, you can book 15 minutes with me, there's no cost for that. And here's an email address, you can email us at info@rx-it.com
Thank you for doing that. Well, thank you everyone. Appreciate your attending our webinar on Key Simple Security Steps and enjoy the rest of your day.
 Please include attribution to rx-it.com with this graphic.
Please include attribution to rx-it.com with this graphic.
Share this Image On Your Site
Subscribe to Rx-IT to watch more videos: www.rx-it.com/videos Connect with BNN Bloomberg: For the latest news visit: https://www.rx-it.com/
Contact Rx-IT here: https://www.rx-it.com/contact/
Rx-IT on Facebook: https://www.facebook.com/RxITtech/
Rx-IT on Twitter: https://twitter.com/rxpc
Rx-IT on LinkedIn: https://www.linkedin.com/company/rx-it-technology-solutions
-- Since 1999, Rx-IT has been a leading provider of IT support and consulting, focusing on small and medium sized businesses in Springfield VA, Arlington VA, Maryland, Boston, Fairfax County VA, Washington DC, NOVA and Suburban MD. We have helped hundreds of businesses increase productivity and profitability by making IT a streamlined part of operations. We equip our clients with customized technology solutions for greater operational value and to reduce risk.
Also, check out these pages.
https://www.rx-it.com/contact/
https://www.rx-it.com/referral-program-for-managed-it-services/